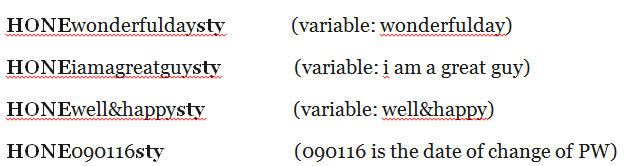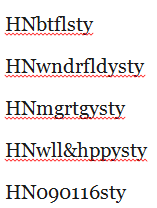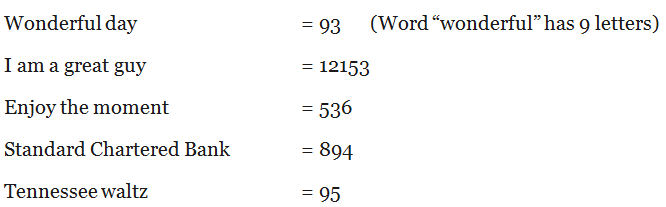Are you using one of those passwords that are described as weak here? http://www.pcworld.com/article/187354/Study_Hacking_Passwords_Easy_As_123456.html
2 Or, you have difficulty creating new passwords when you need to? Unfortunately we cannot avoid it if we want to keep up with the world. Passwords and PINs are really controlling much of our lives nowadays. So much of our work these days, both for business and for personal matters, are carried out on the computers and through the Internet. It means we have to cope with more and more passwords and PINs.
3 Many of us end up using weak passwords because we are always reminded not to write down the passwords but it is impossible to remember all the passwords if we are to also observe the rule that we must have different passwords for different systems/web portal. Here is a method to help overcome the problem.
A simple principle to follow
4 This method starts from the premise that we will have to write the passwords (PWs) and PINs down somewhere. The important thing is that what we write down will not compromise the PWs and PINs. We can do this if we have them made up of two parts, with one part that can be written down and the other commit to memory. I will call the two parts: a variable and a constant. The variable part is what can be written down and it is different for different PWs and PINs. The constant is not written down. It exists strictly only in the memory and it is applied to all the PWs or the PINs. When we need to create a new PW, we only have to think of a word or something for the variable part. And, when we have to change a PW, we only need to change the variable part.
5 For example, if I use the word ‘honesty’ as my constant. The word will be included in all my PWs. To strength the PWs, I will apply it such that a part of it will be at the front as a prefix and the rest of it a suffix. If the word for the variable part is ‘beautiful’, it will look something like this:
I have the prefix in CAP to further strengthen the password.
My other PWs will then be: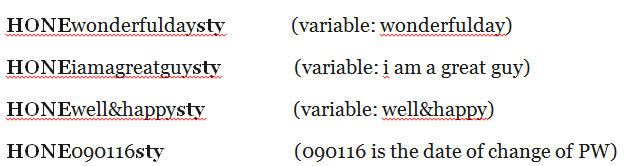
6 I can add a small trick so that the actual PWs become unreadable: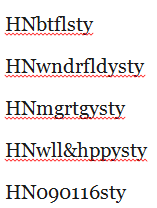
What I have done is to leave out all the vowels.
7 So, all I have to remember is the constant-word ‘honesty’. This way, I can safely write down the variable-words somewhere. My list will look something like this:
I will write the words in their complete forms although I know that the PWs do not contain the vowels.
8 The last example has a mix of alphanumeric characters and this makes the PW even stronger. Hence, it might be a good idea to use a number instead for the variable. Apart from dates, numbers may also be derived from words based on the number counts of the letters in them: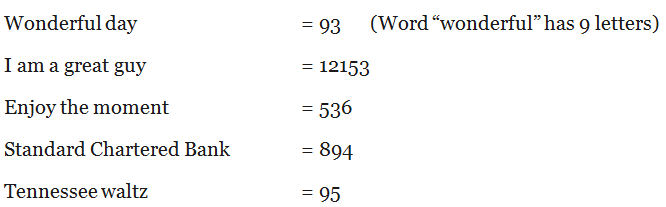
So what are written down are the word phrases that provide the number codes. As can be seen above, the word phrase can also be a public company or a song title.
9 If you are not comfortable with keeping such a list, you can make the list misleading by throwing in some red herrings in the entries. See the post entitled “Red Herrings” what this means.
The Constant
10 The word for the constant is the secret part of the PWs. It is not to be written down. To make it easy for you to recall, use a word that you will never forget because it has a special significance to you and nobody knows it. It may be a word that represents the moral principle you uphold, like honesty. Or, the name of a grandfather or grandmother or other favourite relative, a favourite flower, hero, pet, cartoon character, the first model of car you owned, zodiac/animal sign, DOB in words, etc. Use the imagination and you should be able to come up with a unique one that nobody can guess.
11 Alternatively, a number can be used as a constant. Use one with at least 3 digits and split it into 2 parts for a prefix and a suffix. If you do not have a number that is of special significance to you, you can use a word suggested in the previous paragraph and convert it into a number. Para 14 gives an example of how we can derive a number from a word.
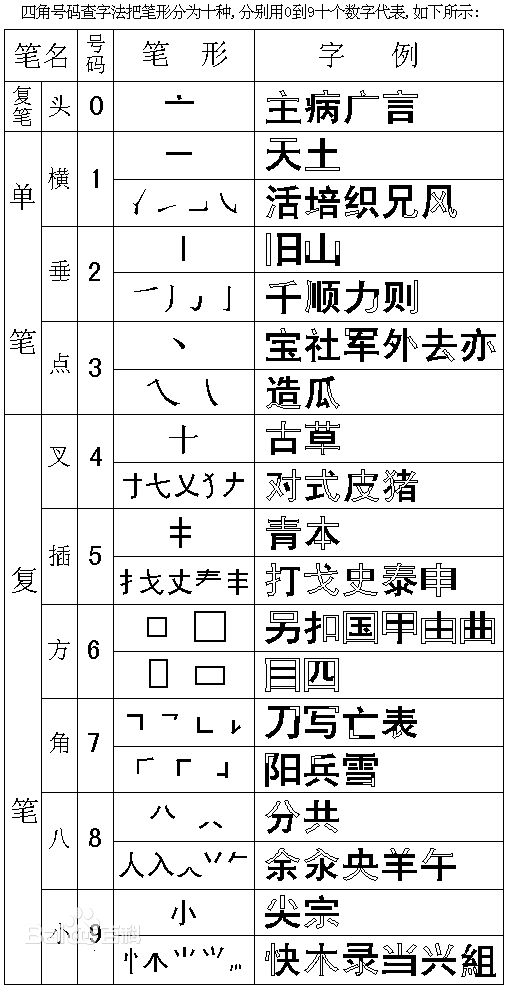
12 For those who know Chinese, they can use a Chinese character or two to represent their constant. I know of two ways to derive numbers from Chinese characters. The easier way is the number of strokes that make up the Chinese character. Since the stroke count for a character will at most be a 2-digit number, then use two characters, one for prefix and another for suffix. The second way is to use the 4 digits from the 4-corner dictionary code. For example, the code for the character for ‘happy’ 樂 is 2290. (More of this in the post Coding With Chinese Characters.)
PIN Numbers
13 For PINs, the constant will of course have to be a number. Like the constant for the PW, it’s a number that you will never forget and thus does not need to be written down. Part of this number will be a prefix and the rest a suffix.
14 To save from having to think of another constant for PIN, you can use the PW constant to work out a number associated with it. One method is to assign a number to each letter of the alphabet based on its position in the alphabet. A number can then be derived for any word by adding the numbers represented by the letters that make up the word. For example, the word ‘honesty’ will be the sum 8+15+14+5+19+20+25 giving the number ‘106’. By this method, the word ‘honesty’ is my constant for both PWs and PINs. I can use ‘honesty’ for PWs and ‘106’ for PINs, or I can use ‘106’ for both.
15 For those who use a Chinese character to represent their password constant, they can obviously use it for PINs as well
16 For the variable, just add a number to make up the number of digits required for the particular PIN. Just like for PWs, it is quite safe to write down the variables in a list for reference, as long as the constant is not written down anywhere – it is strictly only in the memory.
17 It is also important to remember the method you have decided for your coding. I have given several examples of how we can encode the constant and the variables. You should use a coding method for variables different from that used for the constant so that there will be a alphanumeric mix. Decide on just one combination of methods to use and stick to it. We want the system to be effective and yet simple enough to apply and remember.
18 I have not included the use of special characters like ~ ! @ # %, etc. This is because many websites/portals do not accept such characters in the PWs. If it is one that does, they can be included in the constant, and make a note of it in the relevant variable, such as:
I am a great guy!
An exclamation mark is added as a prompt to indicate that a special character is included in the PW but the actual special character is something else.
© Lim Jun Han



 Source:
Source: